Share this article
Introduction.
Data research specialist Gartner Forcasts that worldwide Security Spending will reach $96 Billion in 2018. This should come as no surprise when you consider that the average number of Business Cyber Attacks is now exceeding 4000 a day.
In the current climate, it has never been more essential for businesses to introduce as many Cyber Security Solutions as they can to protect their Business Critical data and Personally Identifiable information. One of these security solutions is called Two-factor Authentication (or 2FA).
But what is Two-Factor Authentication? How does it work and how effective is it at protecting your accounts and your data? Read on to find out more…

Passwords are a common weak spot.
One of the most common Network and Online Security ‘weak spots’ are passwords. As a form of single-factor authentication (SFA) a username and password is an easy target for hackers who are seeking to gain access to private and sensitive data to commit fraudulent acts – with financial information being a primary target.
A strict password policy is essential.
On a Business Network, Network Administrators have the power to put strict password policies in place. This ensures that any passwords created by users must meet a strict Criteria, such as being a minimum length – containing alphanumeric Upper and Lower-case characters and Symbols.
But password policies cannot guarantee your security.
While it’s essential practice to apply a strict password policy in your business, the truth is that ANY password can be hacked. It’s just a case of following best practice and making it as difficult as possible for the hacker to achieve their objective.
However.
There is a popular (and cost-effective) way of addressing username and password vulnerabilities. This form of preventative online security is called ‘Two-factor Authentication’ which a form of Multi-Factor Authentication. Two-factor Authentication is also known as 2FA, TFA and Two-step verification.

What is Two-factor Authentication and how does it work?
As the name suggests, Two-factor Authentication is an enhanced security process that that requires two separate authentication checks to be completed to confirm your identity before you can access your accounts and services. 2FA adds a second layer of authentication that is required after you have entered your username and password.
Examples of 2FA include a one-time password (OPT) that is sent to you via text message, an automated phone call that provides you with an access code, a dedicated 2FA Smartphone App that generates a one-time code, or even a biometric fingerprint scan. We’ll go into more details about these products below.
Two forms of Authentication don’t always equal 2FA.
We stated above that 2FA requires two separate authentication factors. The word ‘separate’ is key here because using two similar forms of authentication is not considered a valid form of 2FA. Two-factor authentication should use two of the following different categories:
- Something you know – Examples: a unique password or code only known by you, an answer to a security question
- Something you have – Examples: a unique one-time password (OTP, or ‘disposable password’) via a Smartphone App, a security token or a text message via your Smartphone
- Something you are – Examples: biometric fingerprint or facial recognition
Different types of 2FA Authentication.
Below are some examples of the most commonly used types of Two-factor Authentication. Each type of 2FA has its advantages and disadvantages.
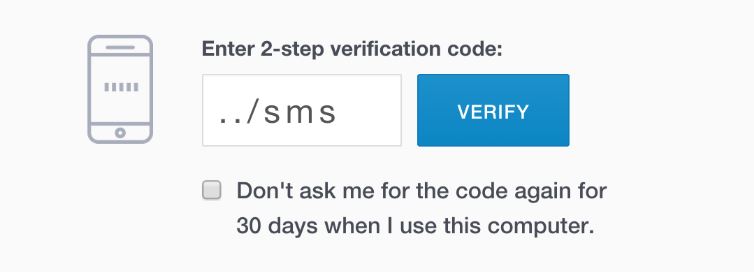
2FA one-time password (OPT) via SMS Text message.
2FA via SMS text message is probably the most convenient form of additional authentication. However, it is also widely considered as the least secure form of 2FA.
Once you’ve logged in with your username and password, you’ll receive a 6-digit code via a Text Message that you’ll also need to type into the login page.
2FA via SMS is one of the most commonly used forms of secondary authentication because of accessibility. Let’s be honest, most of us own a SmartPhone!
What’s the disadvantage of 2FA via SMS?
Although 2FA Authentication via SMS OPT is widely used, many Organisations with stringent information security requirements prefer to use other forms of 2FA because it’s possible for hackers to hijack phone numbers and intercept SMS messages. Another disadvantage is that most popular SmartPhones will display new message notifications on the locked screen, although you should be able to change the security settings on your phone, so the full message isn’t displayed.

2FA one-time password (OPT) via a dedicated Smartphone App.
Another common form of authentication is to obtain a one-time password through a dedicated Authenticator App. Once installed, you can use the App to generate a unique one-time code that can be used to access your account after you’ve logged in with your original username and password.
There’s an App for everything nowadays!
Authenticator apps typically use two different types of authentication. TOTP (time-based one-time authentication) is considered the safest authentication type because each unique code has a short expiry date, whereas HOTP (HMAC-based one-time password) authentication codes have no expiry date. This is incredibly unsafe because your authentication code can be used weeks after being generated.
Examples of different 2FA apps.
Examples of different 2FA apps include Google Authenticator, Authy and Microsoft Authenticator.
 UF2 (Universal 2nd Factor Authentication).
UF2 (Universal 2nd Factor Authentication).
Currently, UF2 is widely considered to be the most secure form of Two-factor Authentication.
UF2 takes 2FA to another level by using USB and NFC security keys as the second form of Authentication. The technology behind UF2 is like that found in Smartcards. According to Wikipedia, the UF2 authentication standard was originally developed by Google and Yubico, with a contribution from a Company called NXP semiconductors. It is now hosted and maintained by the FIDO Alliance, which is the world’s largest Ecosystem for standards-based Interoperable Authentication.
Yubico currently produces UF2 security keys, which are known as Yubikeys! You can find out more about these keys here on the Yubico website.
How does UF2 work?
The main difference between UF2 and other forms of OTP Authentication is that every time you need to access an account that uses 2FA, you’ll need to plug a UF2 USB security key into your computer and press the button on your UF2 key to authenticate alongside your username and password.
If you’re accessing your account via a mobile device, then you’ll need to tap or touch your UF2 key against your registered mobile device to authenticate.
Why is UF2 more secure?
With UF2, the user login is bound to the origin service through a process that’s based on public key cryptography (a public key on the service will need to pair with a private key on the UF2 USB key to authenticate). Putting it simply, this means that only the real site will authenticate with your UF2 key and any attempt to authenticate with a fake site will fail. This greatly mitigates the chances of you becoming a victim of a phishing attack or account breach.
What’s the disadvantage of using UF2?
At the time of writing, UF2 is only compatible with Chrome, Mozilla and Opera browsers and is not compatible with Internet Explorer, Edge, or Safari. According to the Yubico website, ‘Mozilla is currently building support for U2F and Microsoft is working within the FIDO Alliance to bring support to Edge and Windows 10’.
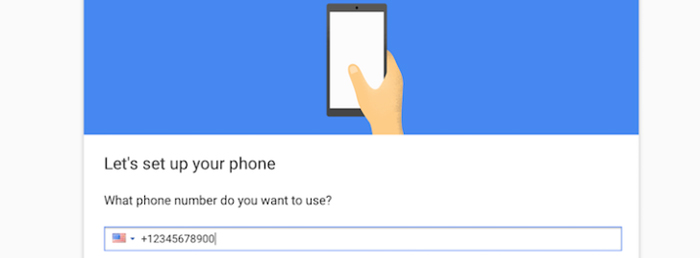 Voice call-based 2FA.
Voice call-based 2FA.
Companies like Google also offer voice call-based Two-factor Authentication, which uses a contact phone number that is tied to the specific account. For example, when using Google call-based Authentication, you’ll receive an automated phone call that provides you with a six-digit reference number that you’ll use to authenticate your identity.
Unlike SMS and App based authentication, your unique code is never digitally displayed on your device, thus further reducing the chances of your account being compromised.
What are the disadvantages of using Voice call-based 2FA?
Like SMS-based 2FA, there is a risk of your call being intercepted. This article on the Symantec website describes how the Android.Banksey Trojan added functionality to its code to enable it to deceive 2FA systems that use voice calls.